This the first in a (possibly never ending) series of examinations into the various types of attacks and scams in the crypto world. If this piece is helpful to you, please let me know on twitter: @CryptoCoinBen.
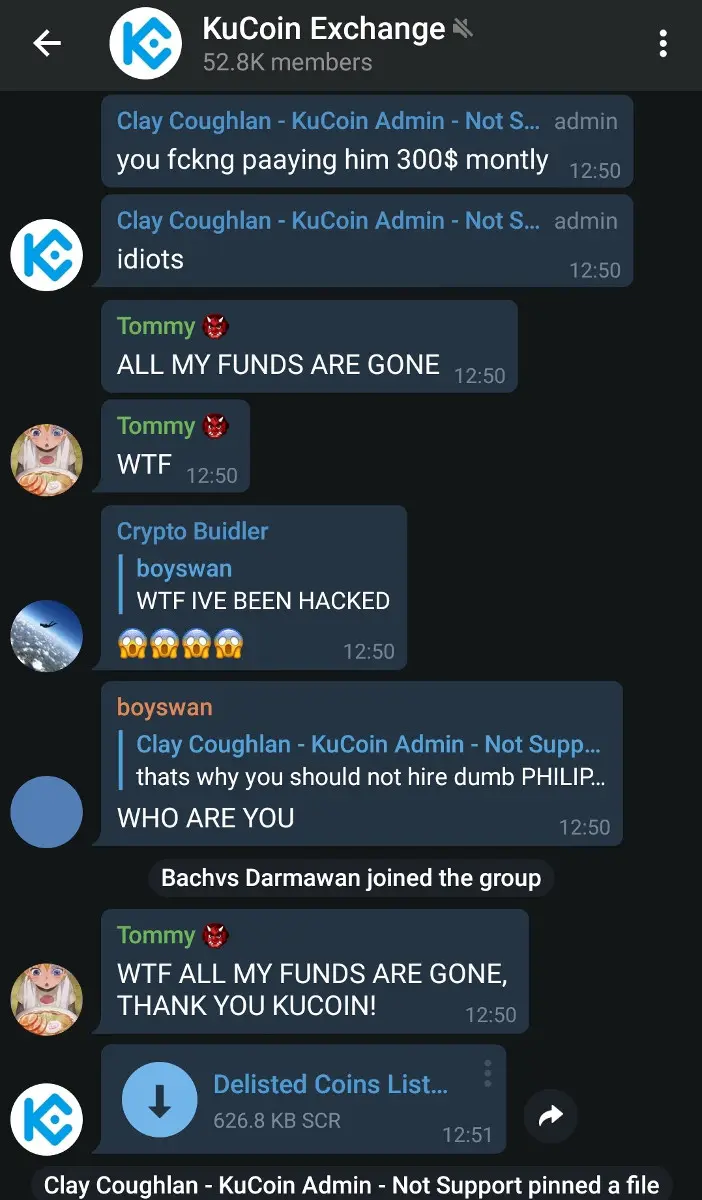
Earlier today a Kucoin community moderators account was compromised. This account was then used to distribute and promote a malicious file in the official Kucoin telegram channel.
(Just for a quick background: Kucoin once was one of the largest crypto exchanges by volume. It is probably still one of the largest exchanges by user accounts. Their official English telegram channel has more than 52,000 members and is managed by a mix of Singapore-based (UTC+8) Administrators and globally-based Community Managers.)
At approximately 1945hrs UTC, a Kucoin Community Manager (‘ClayCoughlan’) posted a link to a malicious .scr file and pinned it to the channel. This sent notifications to the 52k members of that group. While malicious .scr files have been floating around Telegram channels recently, this was unique as it was actively promoted by an account with the ‘admin’ telegram tag.
Dozens of users reported that they ran the file, with some users reporting a loss of funds in the thousands of dollars.
What is an SCR file and what did this SCR file do?
An .scr file is an executable filetype designed to run screensavers on a Windows PC. It is basically the same as a .exe file. It was used here to obfuscate the fact that it was an executable file and to catch naive users off guard.
I had a quick look at the file (I am travelling and without my usual tools). It appears to be a fairly common, low complexity/‘script-kiddie’ malware which collects:
- Hardware, OS and User Information
- Digital Certificates
- Passwords
- URLs visited
More specifically, this malware:
- Has the ability to search the users computer for certain file types.
- Usually, documents and other business sensitive files are searched for, however it would be trivial to look for crypto wallets too.
- Communicates via HTTP(S) to a remote server using a unique ID string for each victim
- Opens up a command and control port (both randomised UDP and TCP) for persistent access later
- Captures keystrokes and communicates these to the remote server
- Hides itself (poorly) and is able to update itself when needed
- Is able to intercept network traffic
- Has the ability to do a bunch of other nasty things to your PC.
Just a quick point on terminology. I do not like to call this a virus. So far it has shown no signs of attempting to self replicate and spread (for example, compromising the victims telegram account and infecting another user). This is best described as a Remote Access Trojan (RAT) or simply Malicious Software (Malware).
Why the attack was successful
- By compromising a Community Managers telegram account, the file appeared to come from a trusted source.
- Why would a ‘Kucoin Admin’ post something malicious? People trusted that user and this exchange.
- By obfuscating the fact it was an executable file, victims were more likely to click on it.
- Most users know not to click on a .exe file (I hope). This was a .scr file however, so they may have thought it was ok.
- Timed to perfection.
- The attack occured at 3:45am China/Singapore time. The in-house Kucoin administrators were expected to be asleep at this time.
- The Community Manager (ClayCoughlan) should have been the only person, with admin access, awake at the time of the attack.
- Another Kucoin Admin did respond about 10 minutes later, which is actually pretty impressive. Although it took another half hour before the posts by the compromised accounts were removed by the other admin.
Damaged caused by the attack
- Dozens of users complained about lost funds from:
- Kucoin accounts
- PC Wallets
- It is possible the compromised computers will be used in future nerferious activities.
- It is possible that other accounts of the victims have been compromised as well (email, banking, etc)
- Compromise is likely to continue if the victims do not take adequate steps to clear it from their PC.
What should affected users do now?
- Consider every wallet you own compromised
- Move your crypt funds to a fresh wallet (Don’t use the compromised PC).
- Consider ever account you own compromised
- Begin resetting every account you own, starting with your exchanges, email, banking and social media accounts (don’t use the compromised PC).
- At minumum, use a trusted antivirus to remove the infection
- Simply deleting files is not good enough, it has already replicated itself and will find ways to hide and relaunch again.
- If you don’t have antivirus, I recommend Malwarebytes to family members (It comes with a free trial version for 14 days, and is reasonably priced if you want to continue using it).
- Ideally, reinstall windows.
How to avoid this style of attack.
- Avoid clicking on unknown files in telegram groups.
- Avoid running your daily user account with admin privledges (You can still have access admin functions, it will just ask for the administrators password).
- Install antivirus software and keep it updated (at minimum, Windows users should use the free Windows Defender).
- Store your crypto in a hardware wallet (Ledger Nano S and Coolwallet are both fantastic products).
- Enable 2FA for all accounts which have this feature (especially banking, finance, email, etc)
Editor-in Chief
Related Posts






Subscribe to our newsletter!
Information